Comprehensive Guide to Cyber Security: Safeguarding Your Digital Assets
In today’s digital age, cyber security is more crucial than ever. As we become increasingly reliant on technology, the threats to our digital assets grow exponentially. From personal data breaches to large-scale corporate hacks, the need for robust security measures is undeniable. This guide will walk you through the various aspects of cyber security, ensuring you have the knowledge to protect your digital world.
1. Firewall Solutions
What are Firewalls?
Firewalls are essential components in network security, acting as barriers between trusted and untrusted networks. They monitor and control incoming and outgoing network traffic based on predetermined security rules.
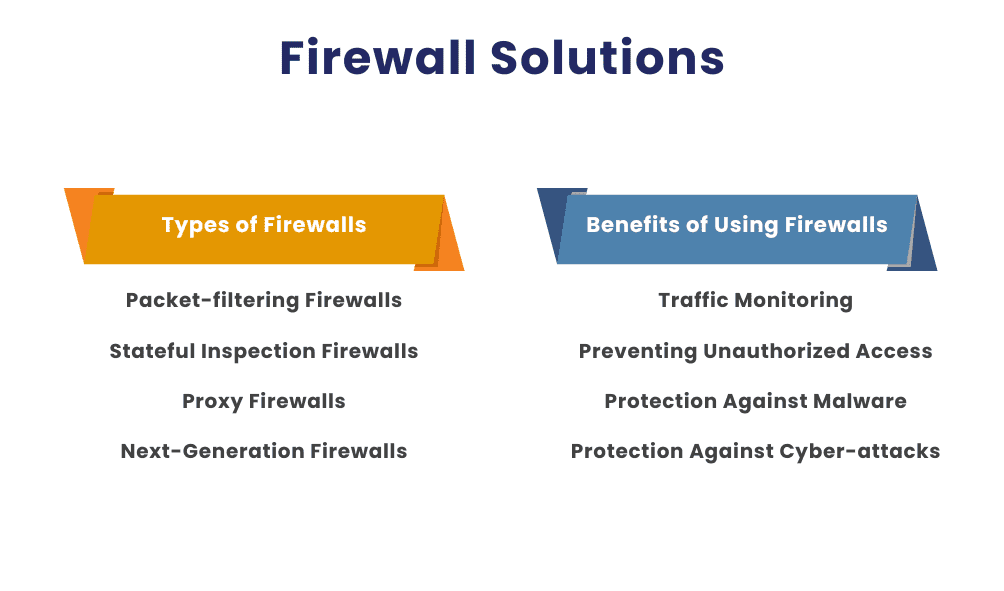
Types of Firewalls
Packet-filtering Firewalls: These are the most basic type of firewalls, which inspect packets and either allow or deny them based on predefined rules.
Stateful Inspection Firewalls: These firewalls track the state of active connections and make decisions based on the state and context of traffic.
Proxy Firewalls: Also known as application-level gateways, these firewalls act as intermediaries for requests from clients seeking resources from other servers.
Next-Generation Firewalls (NGFW): NGFWs offer advanced features such as in-line deep packet inspection, intrusion prevention systems, and application awareness.
Benefits of Using Firewalls
- Traffic Monitoring: Firewalls continuously monitor network traffic, ensuring only authorized data flows in and out.
- Preventing Unauthorized Access: They block unauthorized access to networks and systems, protecting sensitive information.
- Protection Against Malware and Cyber-attacks: Firewalls help prevent malware and cyber-attacks from penetrating the network.
2. Security Proxy Solutions
Security proxies are servers that act as intermediaries for requests from clients seeking resources from other servers, enhancing security and performance.
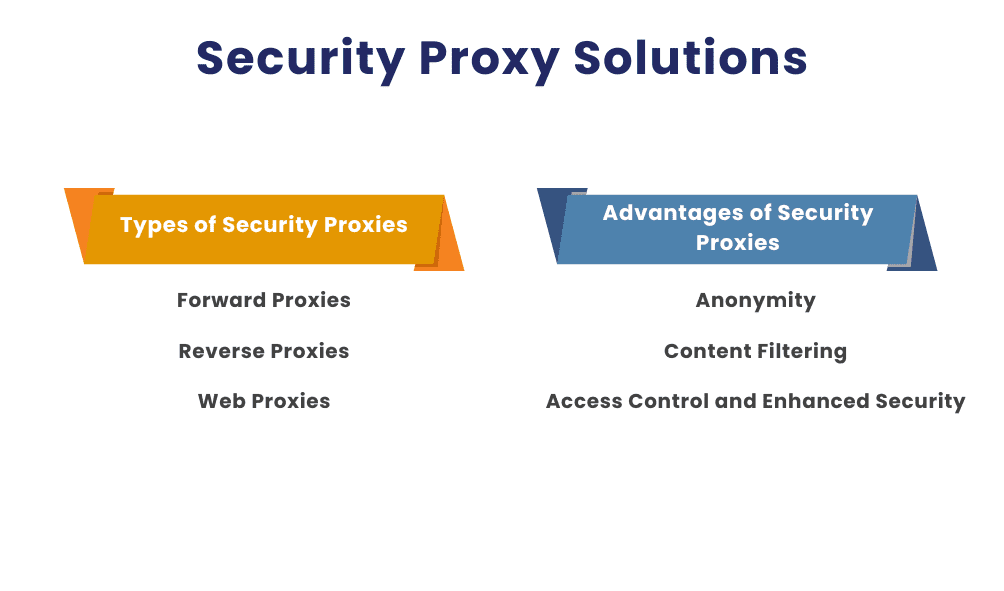
Types of Security Proxies
Forward Proxies: These proxies forward client requests to the internet, often used to bypass geo-restrictions or for caching.
Reverse Proxies: Reverse proxies retrieve resources on behalf of clients from one or more servers, commonly used for load balancing and caching.
Web Proxies: These proxies are specifically designed to handle web requests, providing anonymity and content filtering.
Advantages of Security Proxies
- Anonymity: Security proxies can hide the client’s IP address, providing anonymity.
- Content Filtering: They can filter unwanted content, ensuring users only access safe and appropriate information.
- Access Control and Enhanced Security: Proxies provide an additional layer of security by controlling access and monitoring traffic.
3. Endpoint Security Solutions
Endpoint security focuses on protecting individual devices such as computers, smartphones, and tablets from malicious attacks.
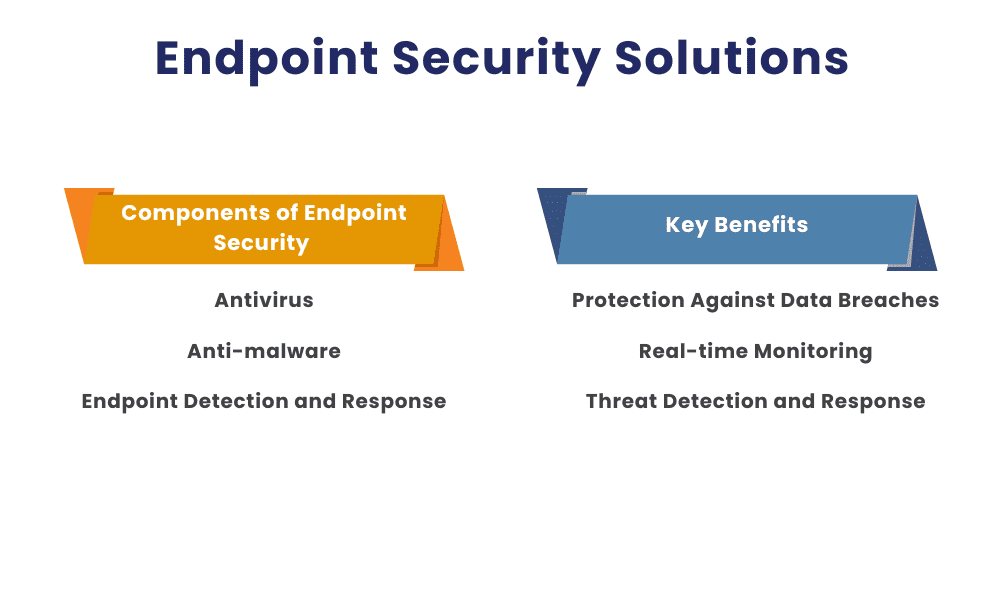
Components of Endpoint Security
Antivirus: Antivirus software detects and removes malicious software from devices.
Anti-malware: Anti-malware provides broader protection against various types of malware, including viruses, worms, and ransomware.
Endpoint Detection and Response (EDR): EDR solutions continuously monitor endpoint activities to detect, investigate, and respond to threats.
Key Benefits of Endpoint Security
- Protection Against Data Breaches: Endpoint security solutions help prevent unauthorized access to sensitive data.
- Real-time Monitoring: Continuous monitoring allows for immediate detection and response to threats.
- Threat Detection and Response: EDR tools enable quick identification and mitigation of security incidents.
4. Data Loss Prevention (DLP)
Understanding DLP
Data Loss Prevention help protect sensitive data by monitoring, detecting, and blocking unauthorized data transfers.
DLP Strategies
Network DLP: Network DLP monitors data in motion across the network, preventing unauthorized transfers.
Endpoint DLP: Endpoint DLP focuses on data stored on and transmitted from individual devices.
Cloud DLP: Cloud DLP secures data stored in cloud environments, ensuring compliance and protection.
Why DLP is Crucial
- Compliance with Regulations: DLP helps organizations comply with data protection regulations such as GDPR and HIPAA.
- Preventing Data Breaches: By monitoring and blocking unauthorized data transfers, DLP solutions help prevent data breaches.
- Safeguarding Intellectual Property: DLP protects sensitive corporate information from being leaked or stolen.
5. SIEM & Log Management Solutions
Security Information and Event Management (SIEM) provide real-time analysis of security alerts generated by applications and network hardware.
Key Features of SIEM
Real-time Monitoring: SIEM solutions continuously monitor network activities for suspicious behavior.
Incident Response: They provide tools and processes to respond to security incidents promptly.
Log Management: SIEM collects, stores, and analyzes log data from various sources.
Benefits of SIEM Solutions
- Centralized Security Management: SIEM solutions offer a unified view of security across the organization.
- Improved Threat Detection: They enhance the ability to detect and respond to threats quickly.
- Enhanced Compliance Reporting: SIEM solutions help meet regulatory compliance requirements by providing detailed reports.
6. Cloud Security Solutions
Cloud security involves protecting data, applications, and infrastructures involved in cloud computing.
Importance of Securing Cloud Environments
With the increasing adoption of cloud services, securing cloud environments is crucial to protect against data breaches and cyber-attacks.
Types of Cloud Security Solutions
Identity and Access Management (IAM): IAM solutions control who has access to cloud resources and under what conditions.
Data Encryption: Encrypting data in transit and at rest ensures that it remains secure even if accessed by unauthorized parties.
Cloud Security Posture Management (CSPM): CSPM solutions help organizations manage and secure their cloud environments by continuously monitoring and assessing security risks.
Advantages of Cloud Security
- Scalability and Flexibility: Cloud security solutions can easily scale to meet the growing needs of an organization.
- Cost-effective Solutions: They often reduce the costs associated with traditional security measures.
- Enhanced Collaboration and Productivity: Secure cloud environments enable safe and efficient collaboration.
Conclusion
At Nextdynamix Tech, we understand the critical importance of cyber security in today’s digital landscape. Protecting your digital assets is not just about implementing individual solutions, but about creating a comprehensive and integrated security strategy. By leveraging advanced technologies such as firewalls, security proxies, endpoint security, data loss prevention, SIEM, and cloud security, we help businesses safeguard their most valuable information.
Our team of experts is dedicated to staying ahead of emerging threats and continuously improving our security offerings to ensure that your business remains protected. We believe in a proactive approach, combining state-of-the-art solutions with expert guidance to enhance your security posture.
Don’t leave your digital assets vulnerable. Consult with Nextdynamix Tech today to assess and strengthen your cyber security measures. Together, we can build a robust defense against cyber threats and ensure the safety and integrity of your digital environment.
FAQs
-
What is the primary purpose of a firewall?
The primary purpose of a firewall is to monitor and control incoming and outgoing network traffic based on predetermined security rules, acting as a barrier between trusted and untrusted networks.
-
How does endpoint security differ from network security?
Endpoint security focuses on protecting individual devices like computers and smartphones, while network security aims to safeguard the entire network infrastructure.
-
Why is data loss prevention (DLP) important for businesses?
DLP is crucial for businesses because it helps protect sensitive data from unauthorized access and breaches, ensuring compliance with regulations and safeguarding intellectual property.
-
What are the benefits of using a SIEM solution?
SIEM solutions offer centralized security management, improved threat detection, real-time monitoring, incident response, and enhanced compliance reporting.
-
How can cloud security solutions enhance productivity?
Cloud security solutions enable safe and efficient collaboration by protecting data and applications in the cloud, ensuring that users can work securely from anywhere.
At Nextdynamix, We Have Pros and Peers for More Insights!
Connect with our professional web and app specialists to achieve impeccable development and seamless execution. Allow us to comprehend your industry obstacles and deliver efficient solutions, unlocking your business potential.
Contact us today for further information