Node.js Security: Protecting Your Applications from Threats and Attacks
Table of Contents
ToggleSecurity is not about risk elimination; it's about risk reduction and acceptance."
- Steve Hultquist
In the realm of modern web development, Node.js has emerged as a powerful and versatile platform for building server-side applications. Its non-blocking, event-driven architecture makes it an excellent choice for handling real-time applications and concurrent connections.
However, like any other technology, Node.js applications are not immune to security threats and attacks. Ensuring the security of your Node.js applications is not just best practice; it's an absolute necessity in today's digital landscape, where cyber threats are on the rise and data breaches can have devastating consequences.
So, in this blog, we will explore the various aspects of Node.js security and discuss best practices to protect your applications from potential vulnerabilities.
Understanding Node.js
Before diving into Node.js security, it's essential to understand what Node.js is and how it works. Node.js is an open-source, cross-platform JavaScript runtime environment that executes JavaScript code on the server side. It is built on Chrome's V8 JavaScript engine and provides an event-driven, non-blocking I/O model, allowing developers to build scalable & high-performance applications.
Node.js is used commonly for building web servers, APIs, and real-time applications such as chat apps and online games. Its lightweight and efficient design has made it a popular choice for developers, but this popularity also makes it a target for malicious actors seeking to exploit vulnerabilities.
Common Security Threats in Node.js
Node.js applications can be vulnerable to a variety of security threats and attacks. It's crucial to be aware of these threats to develop effective security strategies. Here are some common security threats in Node.js:
Injection Attacks
SQL Injection: In Node.js applications that interact with databases, improper user input handling can lead to SQL injection attacks. Attackers can manipulate input data to execute malicious SQL queries, potentially gaining unauthorized access to the database.
Command Injection: Node.js applications that execute system commands can be vulnerable to command injection attacks. If user input is not validated and sanitized appropriately, attackers can inject malicious commands that may lead to unauthorized access or data loss.
Cross-Site Scripting (XSS)
Cross-site scripting is a widespread web application vulnerability. In Node.js, as in other web technologies, XSS occurs when user-generated content is not sanitized appropriately before being displayed on a web page. Attackers can inject malicious scripts into web pages, potentially stealing sensitive information or performing actions on behalf of the user without their consent.
Cross-Site Request Forgery (CSRF)
CSRF attacks target the trust a user has on a website. Attackers trick users into performing actions on a website without their knowledge or consent. Node.js applications can be vulnerable to CSRF if they don't implement proper anti-CSRF mechanisms, allowing attackers to perform actions on behalf of authenticated users.
Insecure Dependencies
Node.js applications often rely on third-party packages and modules from the npm (Node Package Manager) registry. If these dependencies contain security vulnerabilities or are not updated regularly, they can become an entry point for attackers to compromise your application.
Inadequate Authentication and Authorization
Improper user authentication and authorization implementation can lead to unauthorized access to sensitive data or functionalities. Weak passwords, lack of session management, or insufficient access controls can put your Node.js application at risk.
Data Exposure and Information Leakage
Node.js applications may inadvertently leak sensitive information, such as stack traces or configuration details, in error messages. Attackers can exploit this information to gather intelligence about your application's architecture and potential vulnerabilities.
Best Practices for Node.js Security
Let's delve into best practices to protect your applications from these threats now that we've identified common security threats in Node.js.
Input Validation and Sanitization
Properly validate and sanitize all user input, including data received from forms, URLs, and API requests. Use libraries like express validator to validate and sanitize data before processing it. Implement input validation at both the client and server sides to prevent malicious input from reaching your application.
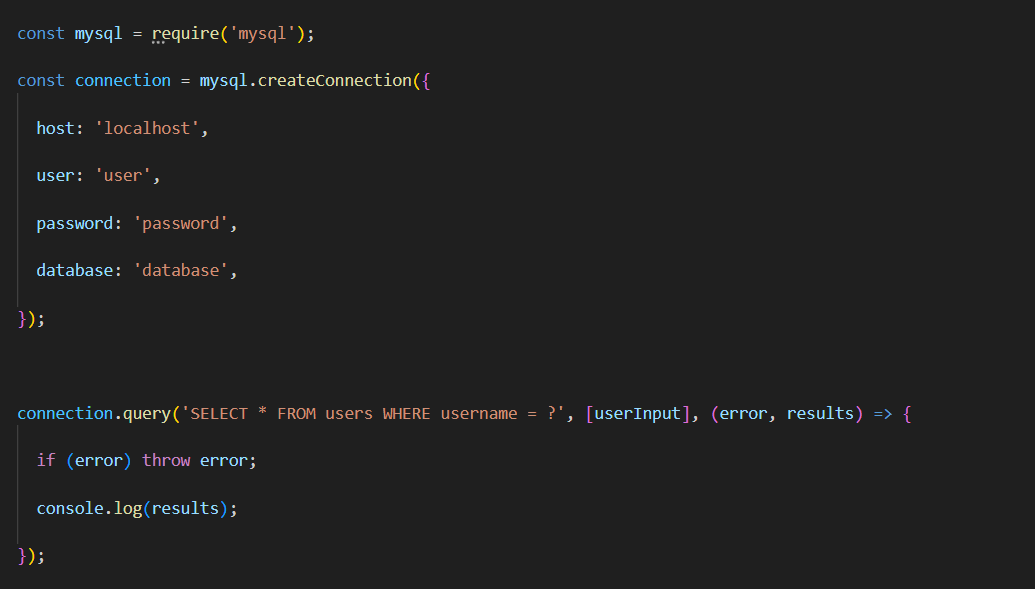
Use Parameterized Queries
You can use parameterized queries or prepared statements to prevent SQL injection attacks while interacting with databases. Parameterized queries separate user input from SQL statements, making it impossible for attackers to inject malicious SQL code.
Here's an example using the MySQL library:
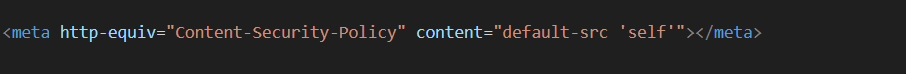
Implement Content Security Policy (CSP)
Implement a Content Security Policy (CSP) in your Node.js application to mitigate XSS attacks. CSP allows you to define which content sources are considered trusted and which are not. It helps prevent the execution of scripts from untrusted sources.
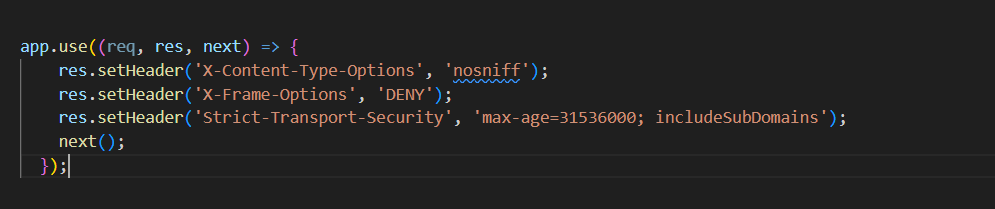
Use Security Headers
Set appropriate security headers in your Node.js application's responses. Headers like X-Content-Type-Options, X-Frame-Options, and Strict-Transport-Security help protect your application from various types of attacks, including clickjacking and MIME sniffing.
Secure Session Management
Implement safe session management using libraries like express session. Store session data securely and use secure cookies to prevent session fixation attacks. Configure session timeouts to reduce the risk of session hijacking.
Use Authentication Libraries
Avoid implementing custom authentication solutions and use well-established authentication libraries like Passport.js. These libraries provide robust authentication mechanisms, including OAuth, JWT, and OAuth2, & regularly update to address security issues.
Regularly Update Dependencies
Keep your Node.js dependencies up to date. Use tools like npm audit to identify and remediate security vulnerabilities in your project's dependencies. You can consider using package-lock.json or yarn.lock to ensure consistent dependency versions across environments.
Implement Rate Limiting and DDoS Protection
Protect your Node.js application from brute force attacks and Distributed Denial of Service (DDoS) attacks by implementing rate limiting and utilizing DDoS protection services. Services like Cloudflare or AWS Shield can help mitigate DDoS attacks.
Monitor and Log Security Events
Implement comprehensive logging and monitoring for your Node.js application. Monitor for suspicious activities, failed login attempts, and other security events. Tools like ELK Stack (Elasticsearch, Logstash, Kibana) can help you centralize and analyze logs effectively.
Conduct Security Audits and Penetration Testing
Regularly perform security audits and penetration testing on your Node.js application. Hire professionals or use automated tools to identify vulnerabilities and weaknesses in your application's security posture. Fix any issues promptly.
Keep Abreast of Security Updates
Stay informed about Node.js security updates and advisories. Subscribe to security mailing lists, follow security blogs, and actively monitor Node.js release notes for security patches and updates.
Conclusion
Node.js is a powerful platform for building server-side applications, but its popularity also makes it a target for security threats and attacks. To protect your Node.js applications from vulnerabilities, you must adopt a proactive approach to security. You can significantly reduce the risk of security breaches by implementing best practices such as input validation, secure session management, and regular dependency updates.
Remember that security is an ongoing process. Regularly assess and enhance the security of your Node.js applications, stay informed about emerging threats, and be prepared to respond to incidents swiftly. By following these best practices, you can build robust and secure Node.js applications that protect both your data and your users.
Thanks for Reading!
Read More on Aelum Blogs
Author: NextDynamix Pvt. Ltd.
At Nextdynamix, We Have Pros and Peers for More Insights!
Connect with our professional web and app specialists to achieve impeccable development and seamless execution. Allow us to comprehend your industry obstacles and deliver efficient solutions, unlocking your business potential.
Contact us today for further information