What is Penetration Testing? 5 Things You Need to Know!
In the ever-evolving landscape of cybersecurity, penetration testing stands out as a critical component in safeguarding sensitive data and systems. But what exactly is penetration testing, and why is it so essential? This blog post delves into the intricacies of testing, highlighting five key aspects you need to understand.
What is Penetration Testing?
Penetration testing, also known as pen testing or ethical hacking, is a simulated cyber-attack against a computer system, network, or web application to identify vulnerabilities that could be exploited by malicious hackers. The goal of testing is to uncover security weaknesses and provide actionable insights to mitigate these risks. For more information, visit Penetration Testing Services.
What is Penetration Testing and Why is Penetration Testing important?
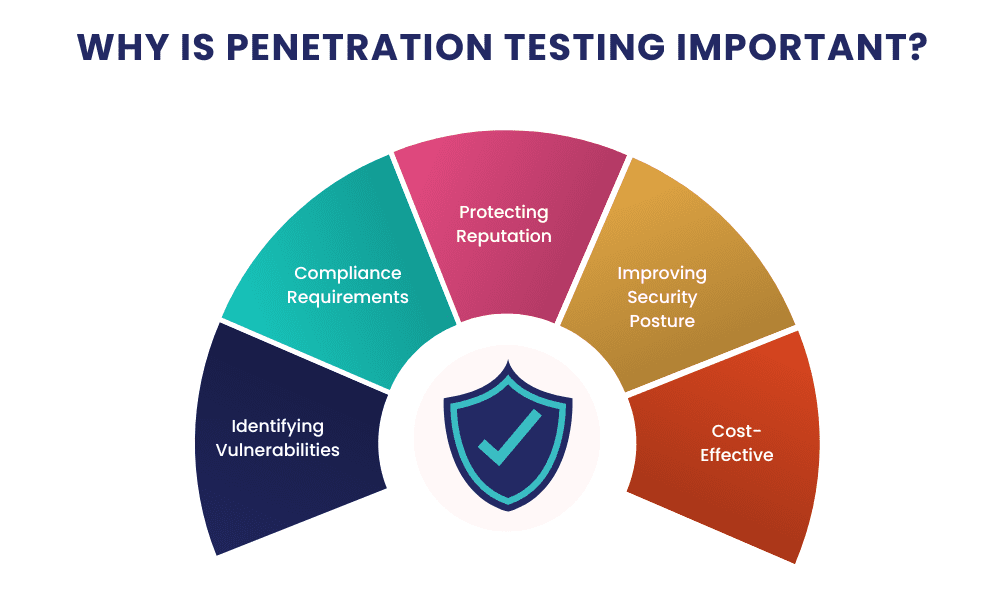
Penetration testing is crucial for several reasons:
- Identifying Vulnerabilities: It helps organizations identify security gaps before attackers can exploit them.
- Compliance Requirements: Many industries have regulatory requirements that mandate regular testing.
- Protecting Reputation: A security breach can damage an organization’s reputation and erode customer trust.
- Improving Security Posture: Regular testing helps organizations stay ahead of potential threats.
- Cost-Effective: Addressing vulnerabilities proactively can save significant costs associated with data breaches and downtime.
Types of Penetration Testing
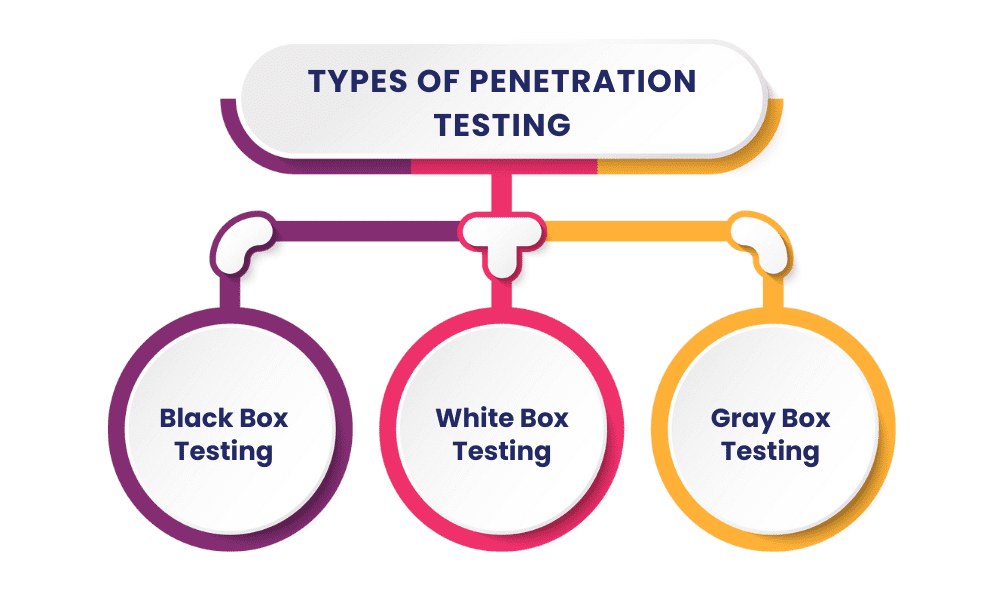
Penetration testing can be categorized into several types based on the scope and methodology:
Black Box Testing
In black box testing, the tester has no prior knowledge of the system being tested. This approach simulates an external attacker’s perspective and aims to identify vulnerabilities that could be exploited without insider information.
White Box Testing
White box testing involves a comprehensive evaluation where the tester has full access to the system’s internal structures, code, and architecture. This type of testing is thorough and can identify vulnerabilities that may not be apparent in black box testing.
Gray Box Testing
Gray box testing is a hybrid approach where the tester has partial knowledge of the system. This method combines elements of both black box and white box testing to provide a balanced perspective on security vulnerabilities.
The Penetration Testing Process
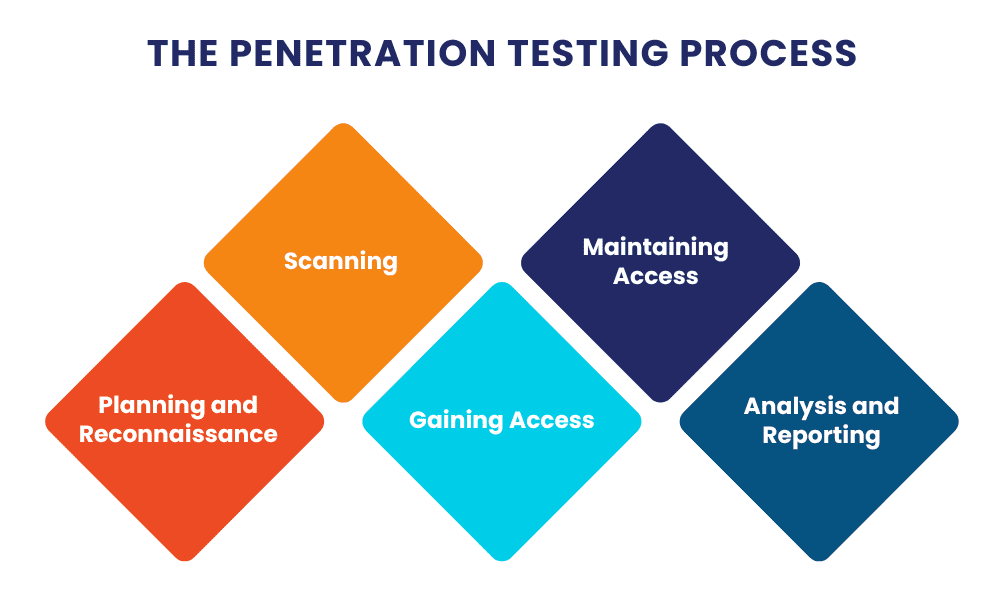
The penetration testing process typically follows a structured approach to ensure thorough evaluation and accurate results:
Planning and Reconnaissance
The first step involves defining the scope and objectives of the test, gathering intelligence about the target system, and identifying potential entry points.
Scanning
In this phase, the tester uses various tools to scan the system for vulnerabilities. This includes network scanning, port scanning, and identifying potential weaknesses.
Gaining Access
The tester attempts to exploit identified vulnerabilities to gain access to the system. This step simulates how an attacker would breach the system’s defenses.
Maintaining Access
Once access is gained, the tester tries to maintain access and move laterally within the system to identify further vulnerabilities.
Analysis and Reporting
The final phase involves analyzing the findings, documenting the vulnerabilities discovered, and providing recommendations for remediation.
Tools Used in Penetration Testing
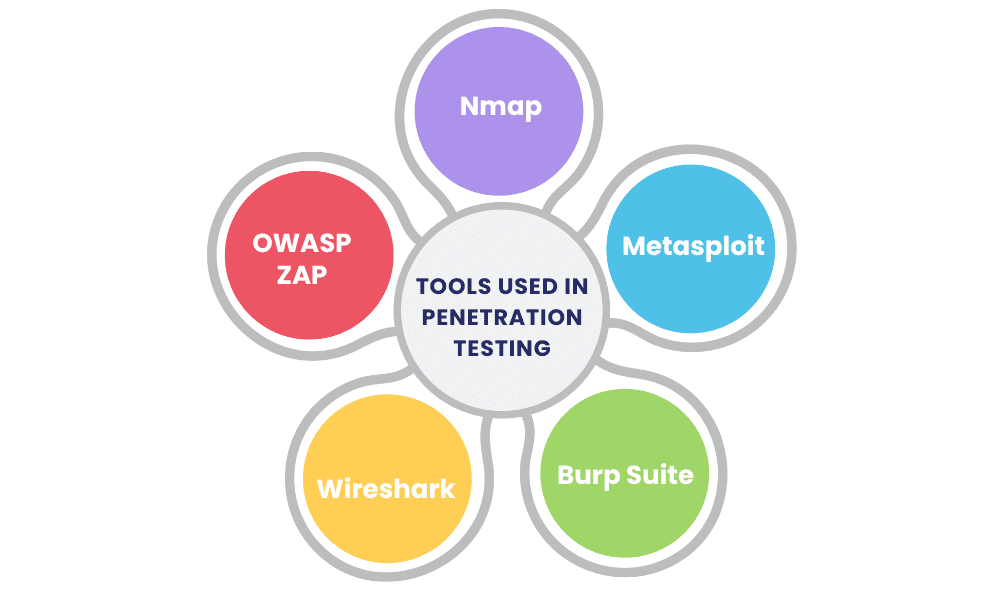
Penetration testers rely on a variety of tools to identify and exploit vulnerabilities. Some commonly used tools include:
Nmap
Nmap (Network Mapper) is an open-source tool used for network discovery and security auditing. It helps identify open ports, services, and potential vulnerabilities.
Metasploit
Metasploit is a popular framework used for developing and executing exploit code against a target system. It is widely used for testing and vulnerability assessment.
Burp Suite
Burp Suite is a comprehensive tool for web application security testing. It includes features for scanning, crawling, and exploiting web application vulnerabilities.
Wireshark
Wireshark is a network protocol analyzer that allows testers to capture and analyze network traffic in real-time. It helps identify potential security issues within network communications.
OWASP ZAP
OWASP Zed Attack Proxy (ZAP) is an open-source tool for finding vulnerabilities in web applications. It is designed to be user-friendly and can be used by both beginners and experienced testers.
Challenges in Penetration Testing
While penetration testing is essential, it comes with its own set of challenges:
Complexity of Modern Systems
As systems become more complex, identifying and exploiting vulnerabilities becomes more challenging. Penetration testers must stay updated with the latest technologies and attack vectors.
False Positives
Penetration testing tools can sometimes generate false positives, which can lead to unnecessary remediation efforts. Testers must validate findings to ensure accuracy.
Limited Time and Resources
Conducting thorough penetration tests requires significant time and resources. Organizations must balance the need for comprehensive testing with available resources.
Evolving Threat Landscape
Cyber threats are constantly evolving, making it difficult to stay ahead of attackers. Continuous learning and adaptation are essential for effective penetration testing.
Best Practices for Penetration Testing
To maximize the effectiveness of penetration testing, organizations should follow these best practices:
Regular Testing
Conduct penetration tests regularly to identify new vulnerabilities and address them promptly. Regular testing helps maintain a strong security posture.
Skilled Testers
Employ skilled and certified penetration testers who have experience with the latest tools and techniques. Skilled testers can provide more accurate and insightful findings.
Comprehensive Reporting
Ensure that penetration test reports are detailed and actionable. Reports should include a clear description of vulnerabilities, their potential impact, and recommendations for remediation.
Collaboration
Foster collaboration between penetration testers and internal security teams. Collaboration helps ensure that findings are understood and addressed effectively.
Continuous Improvement
Use the insights gained from testing to continuously improve security measures. Implement lessons learned to strengthen defenses and reduce the risk of future attacks.
Conclusion
Penetration testing is a vital component of a robust cybersecurity strategy. By understanding the key aspects of penetration testing and following best practices, organizations can identify vulnerabilities, improve their security posture, and protect against potential threats. Regular testing, coupled with skilled testers and comprehensive reporting, ensures that organizations stay ahead in the ever-evolving landscape of cybersecurity.
For more information, visit NextDynamix.
At Nextdynamix, We Have Pros and Peers for More Insights!
Connect with our professional web and app specialists to achieve impeccable development and seamless execution. Allow us to comprehend your industry obstacles and deliver efficient solutions, unlocking your business potential.
Contact us today for further information